Security, Security, Security
The threat landscape for all businesses in the year 2019 has become great. The hackers have gotten very cleaver in their techniques. Here are some of the things the latest Ransomwares could do:
- Some variants are fileless and only stay in memory which means it will not trigger your antivirus software.
- Some variants execute scripts or Microsoft Power Shell commands to embed itself in your system.
- Most variants will find your backup files and permanently delete the backup files from the device they are stored.
- Some Ransomware will purge the Microsoft Shadow Copies and disable the feature on the Windows device.
- Some Malware will sit idle for a period before becoming active.
Here are some scary facts in the Year 2019
- Small and mid-sized businesses are hit by 62% of all cyber-attacks, about 4,000 per day, according to IBM.
- The U.S National Cyber Security Alliance found that 60% of small companies are unable to sustain their businesses over six months after a cyber attack.
- 58% of malware attack victims are categorized as small businesses.
- 38% of malicious attachments are masked as one Microsoft Office type of file or another.
- Small and mid-sized businesses are hit by 62% of all cyber-attacks, about 4,000 per day, according to IBM.
- The U.S National Cyber Security Alliance found that 60% of small companies are unable to sustain their businesses over six months after a cyber attack.
- 58% of malware attack victims are categorized as small businesses.
- 38% of malicious attachments are masked as one Microsoft Office type of file or another.
Things you MUST do to protect your business, your business' reputation and guard yourself against lawsuits.
Firewall - "The gate"
Think of the firewall as the gate leading to your property.
- Must use an enterprise-grade firewall. The days of using a "firewall" from Best Buy or your local internet provider will not be enough.
- Ability to control ingress and egress from your network.
- Ability to monitor the traffic.
- Someone needs to review the firewall logs on a regular basis.
Email Security - "The front door"
Think of the email filter as the next level of your protection before entering your home, your front door.
- Since 96% of malware is delivered via email, your MUST use an email filter.
- The filter must include a SmartLink feature which verifies the embedded link is legitimate and safe.
- Protect against data leakage by preventing sensitive information from being sent like social security numbers, date of birth, credit card numbers, medical information and more.
Antivirus - "The gun under your pillow"
A good antivirus is your last line of defense before harm comes to you and your family, the gun under your pillow.
- The antivirus (AV) must use artificial intelligence to detect zero-day threats. Most AV companies take weeks or months before they detect the latest threats and it will take just as long to develop a remedy. Once the fix is created and tested, it has to be pushed to all of the devices. Question - What happens if the device is offline and a malware has already been downloaded to the device.
- The AV must inspect the raw file. A Word doc or a PDF could have a "backdoor" embedded in the file.
- The AV must inspect all folders on the device. Many AV solutions only look in the Windows folders, the drive's root level or My Documents.
Breach Detection - "The Barking Dog"
Breach detection is like the barking dog in your yard. When something has gotten over the fence and in your yard, you want to be alerted.
Breach detection is key to protecting your systems. Should something get past all of your defenses, you need the ability to detect, understand what was affected and how it got there in the first place.
Backups - "The neighbor"
Your backup is like a good neighbor. Having a good neighbor to call upon when you need help. Good backups will save you from having to pay the ransom.
- Your backup device must prevent the tampering of the backup files.
- Backups must be tested daily.
- The backup solution must be able to detect Ransomware.
- The backups files need to be replicated off-site for redundancy.
- Quick recovery of your server in the event of a failure.
- Ability to "spin up" your server in the cloud (required by HIPAA).
Threat Landscape

Ransomware, Crypto-mining, Botnets, Nation State, Hactivists, Dark Web, Phishing, Tor, Users
Common Passwords of 2018

Top Passwords 2018
Don't be like this person who uses easy passwords
Here are some simple tips
- Use a Password Manager or Password Phrases with mix special characters.
- Change your passwords every 90 days
- Don't use the same password in all of your applications or online websites
- Scan the dark web for your compromised logins and passwords
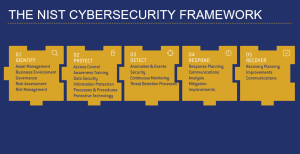
NIST CyberSecurity Framework
The minimum federal government guideline for protecting your network
The 5 critical framework steps
- Identify - A thorough review of your assets, the business environment, which governance are you under, risk assessment and how are you going to manage that risk
- Protect - Protecting your assets requires Access Control, Awareness Training for your staff, how are you going to protect the critical data, develop and maintain the necessary processes and procedures for protecting all of your physical, virtual and intellectual property.
- Detect - Detection of any anomalies and security events happens through continuous monitoring of your network assets and how will you handle the threat detected.
- Respond - Plan the Response and Execute the Plan. Communication to your team, management and document any events in accordance to your compliance requirements.
- Recover - The ability to recover from possible known events and ability to adapt to new threats is critical. Review of your processes and procedures is an ongoing process. Improvement must be the goal.
NIST CyberSecurity Framework
Philosophy For Prevention
Your philosophy For Prevention must include the following steps
- Complete Visibility - You must have full visibility at every level of your network. From the computer, switch, servers and firewall, you must have the means to compile all of the information from logs and alerts, sort through those by severity, assess the threat and formulate a response. Artificial Intelligence helps in this task but human validation is still required.
- Reduce Your Attack Surface - An assessment must be performed to identify where threats may appear. Hopefully you do not have RDP (Port 3389) exposed to the internet. If you do, you are sitting on a time bomb.
- Stop Those Known Threats - A good security specialist should be able to rattle off a list of known threats from the top of their head.
- Prevent Unknown Threats - This is a tricky part. If your attacks surface has been reduced and you are staying up-to-date to the known threats, a good firewall with SIEM solution will be able to identify quickly the new threats.
- Automate Vs Human Validation - Artificial Intelligence helps in sorting through the noise generated but human validation is still required.

Philosophy For Prevention
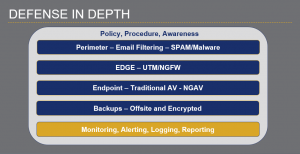
Defense In Depth
Policies, Procedures and Awareness must be developed at every stage of your plan. The monitoring, alerting, logging and reporting is a critical component to protecting your systems. When compliance requirements are in the mix, it is required for you to document those events in case of an audit. The ability to demonstrate you have exercised your due-diligence will go a long way with the federal, state and local authorities.
Defense In Depth
Security Fundamental Blocks
Security is not a one-and-done process. Security requires time, expertise, review, communication and money. When security is done right, everyone will be able to get a good nights sleep.

Security Fundamental Blocks







